In iOS 12, Apple has introduced new password-related features that are designed to make it easier for iPhone and iPad users to create strong, secure, and unique passwords for app and website logins. In this guide, we'll show you how to use two of those features: automatic strong passwords and password auditing.

Automatic strong passwords ensures that if you're prompted by a website or app to make up a password on the spot, Apple will automatically offer to generate a secure one for you. Password auditing meanwhile flags weak passwords and tells you if a password has been reused for different account login credentials. Here's how to use the two features.
How to Use Automatic Strong Passwords in iOS 12
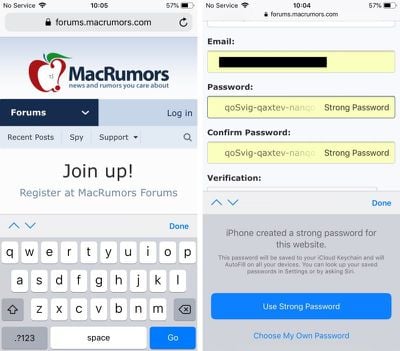
- Launch Safari and navigate to the site asking you to create new login credentials, or launch a third-party app asking you to sign up for a new account.
- Enter a username or email address in the first field.
- Tap on the Password field – iOS will generate a strong password.

- Tap Use Strong Password to accept the password suggestion and save it to your iCloud Keychain.
Pro tip: Next time you need one of your passwords, you can ask Siri. For example, you could say: "Siri, show me my BBC password." Siri will then open up your iCloud Keychain with the relevant entry, but only after you authenticate your identity with a fingerprint, a Face ID scan, or a passcode.
How to Identify Reused Passwords in iOS 12
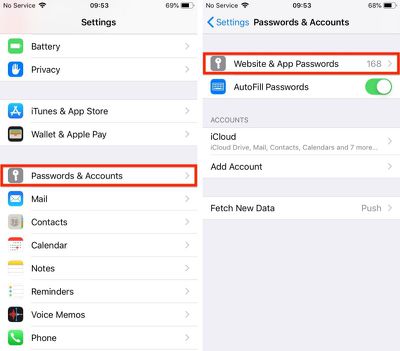
- Launch the Settings app on your iPhone or iPad.
- Tap Passwords & Accounts.

- Authenticate via Touch ID, Face ID, or your passcode.
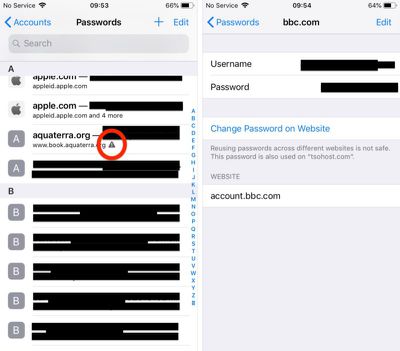
- Scroll down the list of passwords and tap on any entries with a triangular warning symbol.

- Tap Change Password on Website to open the associated website and make the change.
Note that the last screen shows you on which other websites you've used the same password.
Pro tip: You can share passwords with other people directly from the iOS Password Manager via AirDrop. Simply tap the password field and an option to AirDrop the login will appear. The login can be AirDropped to any device running iOS 12 or macOS Mojave.




















Top Rated Comments
The new version using 3 groups of 6 characters has a possible max of (62^6)^3 or 1.83x10^32 combinations.
This assumes that the groups are made up of any of the 26 lower case letters, 26 upper case letters and the 10 digits. If we eliminate i,I,l,L,o,O,1,0 that reduces to 54 possible characters and values of 6.14x10^20 and 1.52x10^31 respectively.
I'm reasonably assured they're not going to get guessed by knowing that the dash is in a particular place.
1) At no time do you, or will you, know your password. So what do you do when you need to use that auto-generated password outside of Safari or something that has access into the Keychain?
2) There is no means to access the saved passwords outside of fully connecting to your iCloud account on an Apple device. So if you lose/damage your iPhone (or iPad or Mac) and don't have another Apple device available you that you are able to connect to iCloud as a primary account you are completely locked out of EVERYTHING until you replace that Apple device with another Apple device. Clever on Apple's part but infuriating the moment the customer realises it.
3) Each time you want to access a password you need to use a credential that protects ALL of your other credentials. This means that primary credential is used more often making it more susceptible to "breach". Credentials are typical most at risk at the point/time of entry so the more you need to use it the more at risk it is.
4) It is all highly presumptive that everything is working right.
This is the world we’re heading to. Away from simple passwords that can be memorized and on to machine-generated passwords which are complex enough to thwart brute-force hacking. Look at SSL/TLS. Sure, these use certificates, but it’s a similar idea. Machine-generated, machine-stored, machine-entered authentication. Personally, I welcome it, as I would argue no one can reasonably generate and remember secure, unique passwords for all of the services they use.
If it doesn’t exist already, this will be a feature of future password managers. It would be trivial to screen-scrape and/or keep a database of password requirements, and generate a compliant password based on that knowledge.