Apple Security
By MacRumors Staff
Apple Security Reviews

Review: Yubico's 5C NFC YubiKey Works Well With Apple's Security Keys Feature
With the launch of iOS 16.3 and macOS 13.2 Ventura, Apple added Security Keys for the Apple ID, offering a more robust way to protect your Apple account and everything associated with your Apple account.
A Security Key is a physical device that works with two-factor authentication. Instead of using a code generated by a secondary Apple device for authentication, when you log into your Apple...
Read Full Article (122 comments)
Apple Security How Tos
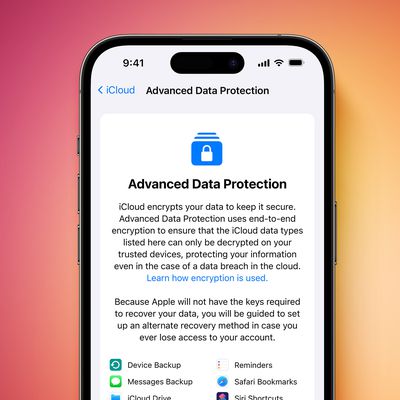
Enable End-to-End Encryption for Your iCloud Backups
Apple's Advanced Data Protection for iCloud feature uses end-to-end encryption to provide the highest level of cloud data security that Apple offers. Here's everything you need to know about enabling it on your devices.
The encrypted security feature gives you the choice to further protect your important iCloud data, including iCloud Backup, Photos, Notes, and more.
Apple's use of...
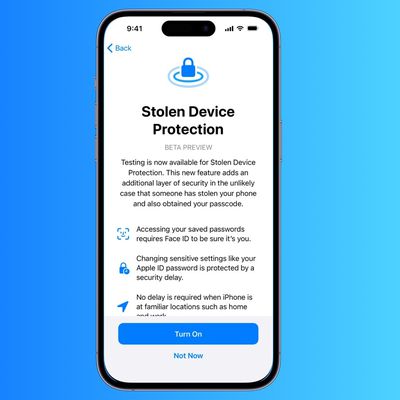
How to Enable Stolen Device Protection on iPhone
When Apple released iOS 17.3 in January, it introduced a Stolen Device Protection feature to provide iPhone users with added security. This article explains what it does, why you might want to turn it on, and how to go about doing so.
In 2023, reports began emerging about a new method thieves were using to steal iPhones and access users' highly sensitive data. Thieves would surreptitiously...

iPhone Displays Green and Orange Dots: What Do They Mean?
Digital privacy is a perennial hot topic these days, and Apple is regarded as being at the forefront of security when it comes to smartphone and tablet operating systems. For example, for an app to access your iPhone or iPad's camera, camera and microphone access must be enabled for the app in question in the Settings app.
Social media apps will often ask you for access to your device's...

How to Share Passwords Among a Group on iPhone and iPad
In iOS 17 and iPadOS 17, Apple has added the ability to securely share passwords and passkeys with people in your contacts using a new shared password function. It's called Family Passwords, and here's how to use it.
Family Passwords allows you to create a group of trusted contacts that you can share passwords and passkeys with across devices. (Passkeys let users sign in to apps and sites...

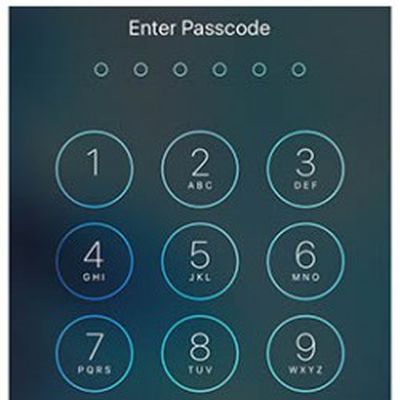
How to Unlock Your iPhone If You Forget Your New Passcode
In iOS 17, if you change your iPhone's passcode and forget it soon after, Apple offers you a 72-hour grace period to fix it without getting locked out of your device. Here's how it works.
In iOS 17 and iPadOS 17, it is now possible to reset an iPhone or iPad's new passcode with the previous passcode you used for up to three days after the change is made. In other words, Apple lets you use...

How to Share Passwords With Friends and Family on iPhone and iPad
In iOS 17 and iPadOS 17, Apple has added the ability to securely share passwords and passkeys with friends and family members using a new shared password function. Here's how to use it.
Family Passwords allows you to create a group of trusted contacts that you can share passwords and passkeys with across devices. (Passkeys let users sign in to apps and sites the same way they unlock their...
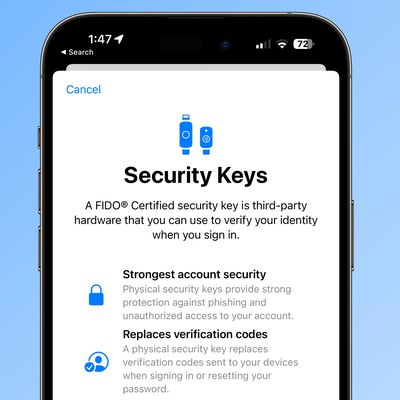
How to Protect Your Apple ID With Security Keys
Apple has introduced security keys as an additional step to help users protect their Apple ID accounts. Keep reading to learn why the alternative authentication method is the most secure method available and what you need to do to set it up.
What Are Security Keys?
With the release of iOS 16.3, iPadOS 16.3, and macOS Ventura 13.2, Apple introduced support for security keys, or physical...

How to Set Up a Stronger Passcode on Your iPhone
Your iPhone's passcode is the first line of defense when it comes to protecting your private data. Here's how to set up a stronger one than the default six-digit passcode that you're likely already using.
If someone with malicious intentions finds out the passcode for your iPhone, they could end up causing you all sorts of trouble. With passcode access to your iPhone's contents, they could...

How to Set Up and Use the Built-in 2FA Code Generator in iOS
With online account hacking becoming increasingly widespread, all users should make sure they're taking every security measure available to them. If you use Apple devices, consider using Apple verification codes to protect your accounts. Keep reading to learn how it works.
One of the best ways to protect any online account is by using two-factor authentication (2FA). 2FA offers hardened...
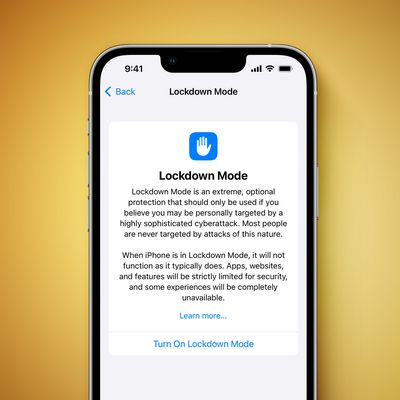
How to Enable Lockdown Mode for Heightened Security on iPhone and iPad
With the release of iOS 16 and iPadOS 16, Apple introduced Lockdown Mode, offering users an "extreme" level of security. This article explains who Lockdown Mode is for, what it does, and how to enable it.
In iOS 16 and iPadOS 16, Apple brought iPhone and iPad users Lockdown Mode, an optional new security feature that's designed to protect users who may be at risk of highly targeted...

How to Use Automatic Strong Passwords and Password Auditing in iOS 12
In iOS 12, Apple has introduced new password-related features that are designed to make it easier for iPhone and iPad users to create strong, secure, and unique passwords for app and website logins. In this guide, we'll show you how to use two of those features: automatic strong passwords and password auditing.
Automatic strong passwords ensures that if you're prompted by a website or app...
Apple Security Articles

Apple's iOS 14.8 Update Fixes Zero-Click Exploit Used to Distribute Pegasus Spyware
Today's iOS 14.8 update addresses a critical vulnerability that Apple engineers have been working around the clock to fix, reports The New York Times.
Last week, The Citizen Lab informed Apple about a new zero-click iMessage exploit targeting Apple's image rendering library. Called FORCEDENTRY, the exploit could infect an iPhone, iPad, Apple Watch, or Mac with the Pegasus spyware, providing...
Security Researchers Unhappy With Apple's Bug Bounty Program
Apple offers a bug bounty program that's designed to pay security researchers for discovering and reporting critical bugs in Apple operating systems, but researchers are not happy with how it operates or Apple's payouts in comparison to other major tech companies, reports The Washington Post.
In interviews with more than two dozen security researchers, The Washington Post collected a number...

Apple Updates Platform Security Guide, Says Kernel Extensions Won't Be Supported on Future Apple Silicon Macs
Apple today shared an updated version of its Platform Security Guide [PDF], providing a comprehensive overview of the latest security advancements across iOS 14, iPadOS 14, macOS Big Sur, tvOS 14, watchOS 7, and more.
For example, the guide provides security details about Safari's optional Password Monitoring feature on iOS 14 and macOS Big Sur, which automatically keeps an eye out for any...
Hackers Discover 55 Apple Vulnerabilities, Awarded Nearly $300,000 in Bounties [Updated]
A group of hackers has been awarded nearly $300,000 by Apple for discovering 55 vulnerabilities in the company's systems.
Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samuel Erb, and Tanner Barnes spent three months hacking Apple platforms and services to discover a range of weaknesses. The 55 vulnerabilities the team discovered were of varying severity, with some being critical.
During ...
Now Patched 'Sign in With Apple' Bug Left Users Open to Attack
Researcher Bhavuk Jain in April discovered a critical Sign in With Apple vulnerability that could have resulted in a takeover of some user accounts. The bug was specific to third party apps that used Sign in With Apple and didn't implement additional security measures.
Jain notes that Sign in With Apple works by authenticating a user through a JWT (JSON Web Token) or a code that's generated...
Apple Says Recently Discovered iOS Mail Vulnerabilities Pose No Immediate Threat, But a Patch Is in the Works
Apple has responded to a recent report on vulnerabilities discovered in its iOS Mail app, claiming the issues do not pose an immediate risk to users.
Earlier this week, San Francisco-based cybersecurity company ZecOps said it had uncovered two zero-day security vulnerabilities affecting Apple's stock Mail app for iPhones and iPads.
One of the vulnerabilities was said to enable an...

Apple Joins the FIDO Alliance to Help Develop and Promote Authentication Standards
Apple has joined the Fast Identity Online (FIDO) Alliance, an open industry association whose mission is to develop and promote stronger authentication standards and help reduce the world's over-reliance on passwords.
Apple joins existing members Amazon, Facebook, Microsoft, Samsung and others in a common goal to secure online connections and support the adoption of the U2F authentication...
Apple Publishes New Apple Platform Security Guide
Coinciding with the launch of its public bug bounty program, Apple today published its new Apple Platform Security guide, offering users details about the security technology and features that are implemented within Apple platforms – including sections on Mac for the first time.
The documentation has been updated to reflect changes in iOS 13.3, iPadOS 13.3, macOS 10.15.2, tvOS 13.3, and...
Apple Officially Launches Public Bug Bounty Program Covering All Apple Software
Apple today officially opened its bug bounty program to all security researchers, after the company announced the expansion plan at the Black Hat conference in Las Vegas earlier this year.
Prior to now, Apple's bug bounty program was invitation-based and non-iOS devices were not included. As reported by ZDNet, from today any security researcher who locates bugs in iOS, macOS, tvOS, watchOS,...

Israeli Security Firm Claims Spyware Tool Can Harvest iCloud Data in Targeted iPhone Attack
An Israeli security firm claims it has developed a smartphone surveillance tool that can harvest not only a user's local data but also all their device's communications with cloud-based services provided by the likes of Apple, Google, Amazon, and Microsoft.
According to a report from the Financial Times [paywalled], the latest Pegasus spyware sold by NSO Group is being marketed to potential...

Researchers and Hackers Use Rare Dev-Fused Prototype iPhones to Unlock Security Secrets
If you've ever wondered how security researchers and hackers manage to bypass Apple's protections and security features to uncover iPhone vulnerabilities and other sensitive info, Motherboard is out today with a new report that has an answer.
Hackers and security researchers use rare "dev-fused" iPhones created for internal use at Apple. These dev-fused iPhones have not finished the production ...

Researcher Gives Apple Details of macOS Keychain Security Flaw Despite No Mac Bug Bounty Program
A German teenager who discovered a macOS Keychain security flaw last month has now shared the details with Apple, after having initially refused to hand them over because of the company's lack of a bug bounty program for the Mac.
Eighteen-year-old Linus Henze dubbed the zero-day macOS vulnerability he found "KeySteal," which, as demoed in the video above, can be used to disclose all...

Apple Says No Personal Data Was Compromised in Australian Teenager Hacking Incident
In a statement, Apple has confirmed that no personal data was compromised by a 16-year-old student from Melbourne, Australia who admitted to hacking into Apple's internal servers on multiple occasions over one year.
The Guardian:At Apple, we vigilantly protect our networks and have dedicated teams of information security professionals that work to detect and respond to threats.
In this...

Security Researchers Find Way to Prevent USB Restricted Mode From Activating on iOS Devices
Security researchers claim to have discovered a loophole that prevents an iPhone or iPad from activating USB Restricted Mode, Apple's latest anti-hacking feature in iOS 12 beta and iOS 11.4.1, which was released on Monday.
USB Restricted Mode is designed to make iPhones and iPads immune to certain hacking techniques that use a USB connection to download data through the Lightning connector to...
FBI Unable to Retrieve Encrypted Data From 6,900 Devices Over the Last 11 Months
The United States Federal Bureau of Investigation was unable to retrieve data from 6,900 mobile devices that it attempted to access over the course of the last 11 months, reports the Associated Press.
FBI Director Christopher Wray shared the number at an annual conference for the International Association of Chiefs of Police on Sunday.
During the first 11 months of the current fiscal year,...
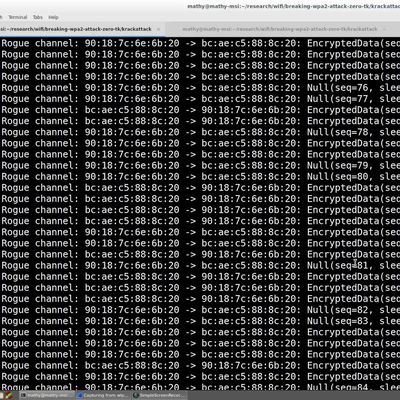
Apple Says 'KRACK' Wi-Fi Vulnerabilities Are Already Patched in iOS, macOS, watchOS, and tvOS Betas
Apple has already patched serious vulnerabilities in the WPA2 Wi-Fi standard that protects many modern Wi-Fi networks, the company told iMore's Rene Ritchie this morning.
The exploits have been addressed in the iOS, tvOS, watchOS, and macOS betas that are currently available to developers and will be rolling out to consumers soon.
A KRACK attack proof-of-concept from security researcher ...

Study Finds Significant Number of Macs Running Out-of-Date Firmware Susceptible to Critical Exploits
A new research paper from Duo Security, shared by Ars Technica, reveals that a significant number of Macs are running out-of-date EFI versions, leaving them susceptible to critical pre-boot firmware exploits.
The security firm analyzed 73,324 Macs used in production environments and found that, on average, 4.2 percent of the systems were running the incorrect EFI version relative to the...

Apple's Latest Transparency Report Shows Jump in National Security Requests
Apple this week released its latest transparency report [PDF] outlining government data requests received from January 1, 2017 to June 30, 2017.
In the United States, Apple received 4,479 requests for 8,958 devices and provided data 80 percent of the time (in 3,565 cases). Worldwide, Apple received 30,814 requests for data from 233,052 devices and provided data 80 percent of the time (in...

Hacker Releases Firmware Decryption Key for Apple's Secure Enclave
A hacker released what he claimed to be a firmware decryption key for Apple's Secure Enclave on Thursday, initially sparking fears that iOS security had been compromised.
Apple's Secure Enclave Processor (SEP) handles all cryptographic operations for the Apple Watch Series 2, the A7 processor that powers the iPhone 5s, the iPad Air, the iPad mini 2 and 3, and subsequent A-series chips. The...
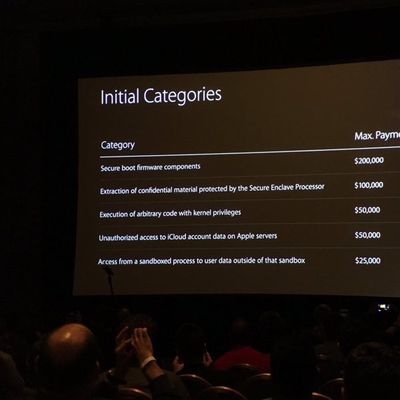
Security Researchers Don't Think Apple Pays Enough for Bug Bounties
Apple's bug bounty program has been available to select security researchers for almost a year now, but according to a new report from Motherboard, most researchers prefer not to share bugs with Apple due to low payouts. More money can be obtained from third-party sources for bugs in Apple software.
"People can get more cash if they sell their bugs to others," said Nikias Bassen, a security...













