As the end of 2024 nears, we are revisiting some of our most-viewed stories of the year. One of them was Apple announcing a new post-quantum cryptographic protocol for iMessage called PQ3. Apple said this "groundbreaking" and "state-of-the-art" protocol provides "extensive defenses against even highly sophisticated quantum attacks."

Apple believes PQ3's protections "surpass those in all other widely deployed messaging apps," according to its February 2024 blog post:
Today we are announcing the most significant cryptographic security upgrade in iMessage history with the introduction of PQ3, a groundbreaking post-quantum cryptographic protocol that advances the state of the art of end-to-end secure messaging. With compromise-resilient encryption and extensive defenses against even highly sophisticated quantum attacks, PQ3 is the first messaging protocol to reach what we call Level 3 security — providing protocol protections that surpass those in all other widely deployed messaging apps. To our knowledge, PQ3 has the strongest security properties of any at-scale messaging protocol in the world.
Apple said PQ3 would be gradually rolling out for supported iMessage conversations starting with its iOS 17.4, iPadOS 17.4, macOS 14.4, and watchOS 10.4 software updates, all of which were released to the public in March this year.
Apple said PQ3 would fully replace iMessage's existing cryptography protocol within all supported conversations later in 2024. All devices in an iMessage conversation must be updated to the above software versions or later to be eligible.
Post-Quantum Cryptography
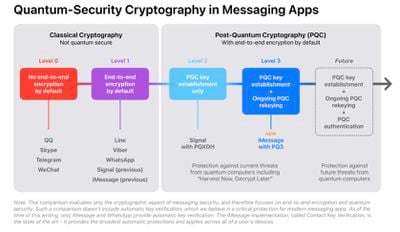
iMessage already supports end-to-end encryption, but existing cryptographic protocols that are commonly used by messaging apps rely on mathematical problems that could potentially be solved by future quantum computers.
PQ3 is designed to protect users against "Harvest Now, Decrypt Later" attacks, in which malicious actors collect large amounts of encrypted data now and store it in hopes they will be able to decrypt it with a quantum computer in the future:
Although such quantum computers don't yet exist, extremely well-resourced attackers can already prepare for their possible arrival by taking advantage of the steep decrease in modern data storage costs. The premise is simple: such attackers can collect large amounts of today's encrypted data and file it all away for future reference. Even though they can't decrypt any of this data today, they can retain it until they acquire a quantum computer that can decrypt it in the future, an attack scenario known as Harvest Now, Decrypt Later.
Apple says PQ3 achieves what it calls "Level 3" security, meaning it secures "both the initial key establishment and the ongoing message exchange."
For deeply technical details about the protocol, read the Apple Security Research blog post.