Root Access Sudo Bug Found to Affect macOS Big Sur
A sudo bug that can grant an attacker root access has been discovered to affect macOS Big Sur (via ZDNet).
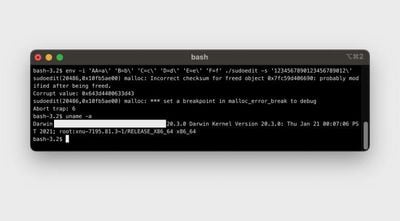
The security vulnerability, identified last week as "CVE-2021-3156" by the Qualys Security Team, affects sudo, which is a program that allows users to run commands with the security privileges of another user, such as an administrator. The bug triggers a "heap overflow" in sudo that changes the current user's privileges to enable root-level access. This can give an attacker access to the entire system. An attacker would need to gain low-level access to a system first to be able to exploit the bug, such as via planted malware.
Sudo is part of many Unix-like systems, including macOS, but it was initially unknown if the vulnerability affected Mac machines since it was only tested by Qualys on Ubuntu, Debian, and Fedora. Security researcher Matthew Hickey has now confirmed that the most recent version of macOS, macOS Big Sur 11.2 can be subject to the sudo attack.
Last week, there was speculation that the macOS Big Sur 11.2 update may address the sudo vulnerability, though it was not definitively known at the time if the bug would affect macOS. While it was found that sudo was left unchanged in macOS Big Sur 11.2, it is now clear that macOS is affected by the exploit.
With some minor modifications, Hickey found that the sudo bug could be used to grant attackers access to macOS root accounts, and the discovery has now been verified by Carnegie Mellon University vulnerability analyst Will Dormann.
Apple has reportedly been notified of the CVE-2021-3156 vulnerability, and due to the severity of the issue, a patch will likely be released soon.
Popular Stories
While the iPhone 17 Pro and iPhone 17 Pro Max are not expected to launch until September, there are already plenty of rumors about the devices.
Below, we recap key changes rumored for the iPhone 17 Pro models as of April 2025:
Aluminum frame: iPhone 17 Pro models are rumored to have an aluminum frame, whereas the iPhone 15 Pro and iPhone 16 Pro models have a titanium frame, and the iPhone ...
Apple may have updated several iPads and Macs late last year and early this year, but there are still multiple new devices that we're looking forward to seeing in 2025. Most will come in September or October, but there could be a few surprises before then.
We've rounded up a list of everything that we're still waiting to see from Apple in 2025.
iPhone 17, 17 Air, and 17 Pro - We get...
Apple is preparing a "bold" new iPhone Pro model for the iPhone's 20th anniversary in 2027, according to Bloomberg's Mark Gurman. As part of what's being described as a "major shake-up," Apple is said to be developing a design that makes more extensive use of glass – and this could point directly to the display itself.
Here's the case for Apple releasing a truly all-screen iPhone with no...
The first iOS 19 beta is less than two months away, and there are already a handful of new features that are expected with the update.
Apple should release the first iOS 19 beta to developers immediately following the WWDC 2025 keynote, which is scheduled for Monday, June 9. Following beta testing, the update should be released to the general public in September.
Below, we recap the key...
Apple's upcoming foldable iPhone (or "iPhone Fold") will feature two screens as part of its book-style design, and a Chinese leaker claims to know the resolutions for both of them.
According to the Weibo-based account Digital Chat Station, the inner display, which is approximately 7.76 inches, will use a 2,713 x 1,920 resolution and feature "under-screen camera technology." Meanwhile, the...
A common complaint about the iPad Pro is that the iPadOS software platform fails to fully take advantage of the device's powerful hardware.
That could soon change.
Bloomberg's Mark Gurman today said that iPadOS 19 will be "more like macOS."
Gurman said that iPadOS 19 will be "more like a Mac" in three ways:Improved productivity
Improved multitasking
Improved app window management...
Apple is working on a new version of the Vision Pro with two key advantages over the current model, according to Bloomberg's Mark Gurman.
Specifically, in his Power On newsletter today, Gurman said Apple is developing a new headset that is both lighter and less expensive than the current Vision Pro, which starts at $3,499 in the U.S. and weighs up to 1.5 pounds.
Gurman said Apple is also...
Apple has confirmed that it will be permanently closing its retail store in the heart of Bristol, England, and there is no replacement in sight.
Apple Bristol in 2023
Apple Bristol will be closing its doors on Saturday, August 9, due to redevelopment plans at the Cabot Circus Shopping Centre, and the adjacent Bristol Shopping Quarter. According to news reports, and a building application, the ...
Apple today updated its vintage products list to add the 2018 Mac mini and the iPhone 6s, devices that will get more limited service and repairs now that they are considered vintage.
The iPhone 6s initially launched in 2015, but Apple kept it around as a low-cost device until 2018, which is why it is only now being added to the vintage list. The iPhone 6s had Apple's A9 chip, and it was...