A USB-based vulnerability that allows for the brute forcing of a passcode on an iOS device has been discovered by security researcher Matthew Hickey, reports ZDNet.
The method, which bypasses the 10-entry attempt that erases an iOS device when the setting is enabled, allows a hacker to plug an iPhone or iPad into a computer and send all passcodes, from 0000 to 9999, all at once, triggering an input routine that takes priority over anything else on the device. Hickey demos the hack in the video below.
"Instead of sending passcodes one at a time and waiting, send them all in one go," he said.
"If you send your brute-force attack in one long string of inputs, it'll process all of them, and bypass the erase data feature," he explained.
All that's required to use this brute force password cracking method is an iPhone or iPad that's turned on and locked and a Lightning cable, according to Hickey. It works on iOS devices up to iOS 11.3.
Hickey's iPhone cracking method takes between three and five seconds for each four-digit passcode, which means it's slow and not as advanced as other passcode cracking methods employed by companies like Grayshift, which makes the GrayKey box. For this method to guess a six-digit passcode, Hickey says it would take weeks.
Apple in iOS 12 is introducing a new USB Restricted Mode that may put a stop to the vulnerability that Hickey has discovered, as well as vulnerabilities exploited by tools like the GrayKey Box.
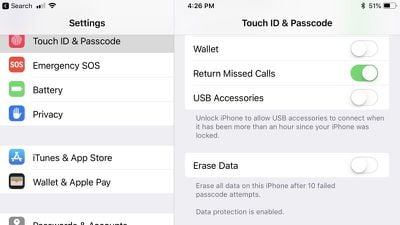
With USB Restricted Mode, enabled by default on iOS devices running iOS 12, USB access to an iPhone or iPad is cut off if it's been more than an hour since the device was last unlocked.
That means computers and other accessories can't be used to access a locked iPhone if it's been locked for over an hour, disabling access via a USB to Lightning cable.
Update: In a statement obtained by iMore, Apple says "the recent report about a passcode bypass on iPhone was in error, and a result of incorrect testing."





















Top Rated Comments
Opens settings > general > about > version
Sees 11.4, close settings and move on with life.
Apple has different employees who do different things. What you’re suggesting here is like asking a school custodian to take over a classroom from a teacher.
[doublepost=1529717755][/doublepost]The iOS 11.4 security content notes ('https://support.apple.com/en-us/HT208848') don’t specify anything seemingly related to this bug.
Maybe instead of just coming up with ideas, Apple needs to have a team who’s job is to try to break or break into every Apple device. They should be full time employed with their sole mission being to find and exploit every possible weakness.
Between the root bug and ones like this, one wonders how many others are out there.
1 attempt takes 4 seconds, that means a 16 digit alphanumeric passcode with upper- and lower case, numbers, and two symbols will take up to 64^16=7,922816251e28 seconds which is in practice never. Unless you can run a dictionary attack or something.
With the brute force attempts an alphanumeric passcode is the only solution to stay safe.
[doublepost=1529735909][/doublepost]That is exactly why I want eSIM in the iPhone and passcode requirement when switching your phone off + auto restart after force shut down.