Robert Xiao, a computer science student at Carnegie Mellon, recently discovered a vulnerability in LocationSmart's website that made the real-time location of millions of phones readily available to anyone with the knowhow.

For background, LocationSmart is a company that collects location data of mobile customers from major carriers, including Verizon, AT&T, Sprint, and T-Mobile in the United States, and then sells it to other companies for a range of purposes, including compliance, cybersecurity, and proximity marketing.
Up until the vulnerability was discovered, LocationSmart offered a trial webpage that allowed anyone to enter their phone number, confirm the request via SMS or a phone call, and view their approximate real-time location.
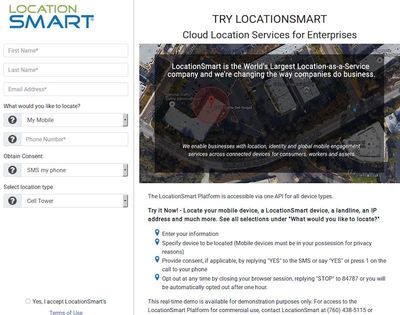
The problem, as Xiao discovered, was that the webpage had a bug that allowed anyone with the technical skills to bypass the phone number verification process and view the real-time location of any subscriber to most major carriers in the United States, in addition to Bell, Rogers, and Telus in Canada.
In a blog post, Xiao said the bug essentially involves requesting the location data in JSON format, instead of the default XML format:
If you make the same request with requesttype=locreq.json, you get the full location data, without receiving consent. This is the heart of the bug. Essentially, this requests the location data in JSON format, instead of the default XML format. For some reason, this also suppresses the consent (“subscription”) check.
Upon discovering the vulnerability, Xiao immediately contacted the US-CERT to coordinate disclosure, and shared details with Brian Krebs, who published a story with further details on his blog Krebs on Security.
Xiao told Krebs that he was able to obtain the approximate longitude and latitude of five different people who agreed to be tracked, coming within 100 yards and 1.5 miles of their then-current locations, all in a matter of seconds. LocationSmart plotted the coordinates on a Google Street View map.
"I stumbled upon this almost by accident, and it wasn't terribly hard to do," Xiao said. "This is something anyone could discover with minimal effort. And the gist of it is I can track most peoples’ cell phone without their consent."
Xiao said his tests showed he could reliably query LocationSmart's service to ping the cell phone tower closest to a subscriber's mobile device. Xiao said he checked the mobile number of a friend several times over a few minutes while that friend was moving. By pinging the friend's mobile network multiple times over several minutes, he was then able to plug the coordinates into Google Maps and track the friend’s directional movement.
It's not clear exactly how long LocationSmart has offered its trial service or how long it has been vulnerable. Krebs linked to an archived version of the website that suggests it dates back to at least January 2017.
When reached for comment via phone, LocationSmart's founder and CEO Mario Proietti told Krebs that the company was investigating.
"We don't give away data," Proietti said. "We make it available for legitimate and authorized purposes. It's based on legitimate and authorized use of location data that only takes place on consent. We take privacy seriously and we’ll review all facts and look into them."
A spokesperson for AT&T told Krebs that the carrier "does not permit the sharing of location information without customer consent or a demand from law enforcement," while Verizon, Sprint, and T-Mobile all pointed towards their privacy policies.
LocationSmart was already in the news prior to this relevation. The New York Times last week reported that Cory Hutcheson, a former Missouri sheriff, was charged with using a private service called Securus, which obtained data from LocationSmart, to track people's phones without court orders.
Those headlines are what prompted Xiao to poke around LocationSmart's website and ultimately discover this vulnerability. However, while the page has been taken down, it's unclear what steps will be taken next if any. At least one U.S. senator has urged the FCC to enforce stricter privacy laws on carriers.
More Coverage: A bug in cell phone tracking firm's website leaked millions of Americans' real-time locations by ZDNet's Zack Whittaker
Update: The FCC's Enforcement Bureau has confirmed it will investigate LocationSmart, according to CNET.