There appears to be a serious bug in macOS High Sierra that enables the root superuser on a Mac with a blank password and no security check.
The bug, discovered by developer Lemi Ergin, lets anyone log into an admin account using the username "root" with no password. This works when attempting to access an administrator's account on an unlocked Mac, and it also provides access at the login screen of a locked Mac.
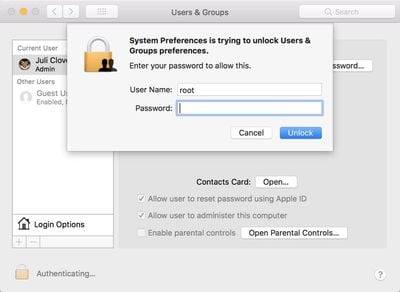
To replicate, follow these steps from any kind of Mac account, admin or guest:
1. Open System Preferences
2. Choose Users & Groups
3. Click the lock to make changes
4. Type "root" in the username field
5. Move the mouse to the Password field and click there, but leave it blank
6. Click unlock, and it should allow you full access to add a new administrator account.
At the login screen, you can also use the root trick to gain access to a Mac after the feature has been enabled in System Preferences. At the login screen, click "Other," and then enter "root" again with no password.
This allows for admin-level access directly from the locked login screen, with the account able to see everything on the computer.
It appears that this bug is present in the current version of macOS High Sierra, 10.13.1, and the macOS 10.13.2 beta that is in testing at the moment. It's not clear how such a significant bug got past Apple, but it's likely this is something that the company will immediately address.
Until the issue is fixed, you can enable a root account with a password to prevent the bug from working. We have a full how to with a complete rundown on the steps available here.
Update: An Apple spokesperson told MacRumors that a fix is in the works:
"We are working on a software update to address this issue. In the meantime, setting a root password prevents unauthorized access to your Mac. To enable the Root User and set a password, please follow the instructions here: https://support.apple.com/en-us/HT204012. If a Root User is already enabled, to ensure a blank password is not set, please follow the instructions from the 'Change the root password' section."
Update 2: Apple released a security update to address the vulnerability on Wednesday morning. The update can be downloaded on all machines running macOS 10.3.1 using the Software Update mechanism in the Mac App Store. Apple says it will automatically push out the update to all users who have not installed it later in the day.
In a statement provided to MacRumors, Apple said the company's engineers began working on a fix as soon as the problem was discovered. Apple also apologized for the vulnerability and said its development process is being audited to prevent something similar from happening in the future.
Security is a top priority for every Apple product, and regrettably we stumbled with this release of macOS.
When our security engineers became aware of the issue Tuesday afternoon, we immediately began working on an update that closes the security hole. This morning, as of 8 a.m., the update is available for download, and starting later today it will be automatically installed on all systems running the latest version (10.13.1) of macOS High Sierra.
We greatly regret this error and we apologize to all Mac users, both for releasing with this vulnerability and for the concern it has caused. Our customers deserve better. We are auditing our development processes to help prevent this from happening again.
All users should download the new security update immediately.





















