Brazilian software developer Matheus Mariano appears to have discovered a significant Disk Utility bug that exposes the passwords of encrypted Apple File System volumes in plain text on macOS High Sierra.
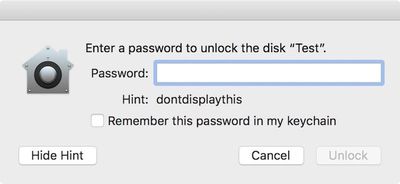
Mariano added a new encrypted APFS volume to a container, set a password and hint, and unmounted and remounted the container in order to force a password prompt for demonstration purposes. Then, he clicked the "Show Hint" button, which revealed the full password in plain text rather than the hint.
MacRumors reproduced this behavior on a 2016 MacBook Pro running macOS High Sierra, including versions 10.13 and 10.13.1 beta. German software developer Felix Schwarz also shared a video of the issue on Twitter today.
Tried myself & it's true: #HighSierra shows the #APFS volume password as hint. Persists reboots, not stored in keychain. Wow. Just wow. pic.twitter.com/FkcHI9KHl9 — Felix Schwarz (@felix_schwarz) October 5, 2017
For clarity, this appears to be a bug within Disk Utility itself. When creating an encrypted APFS volume in Terminal with the diskutil command line utility, the actual hint is shown, rather than the password.
Mariano said he has reported the vulnerability to Apple. The company did not immediately respond to our request for a comment on the matter, but we'll update this article if we hear back.
Update: Apple has addressed this bug by releasing a macOS High Sierra 10.13 Supplemental Update, available from the Updates tab in the Mac App Store. Apple has also shared a support document outlining steps to back up, erase, and restore the encrypted APFS volume upon updating.
The bug has also been fixed in the base version of macOS High Sierra for those who have yet to install the full software update.