Security Researchers Don't Think Apple Pays Enough for Bug Bounties
Apple's bug bounty program has been available to select security researchers for almost a year now, but according to a new report from Motherboard, most researchers prefer not to share bugs with Apple due to low payouts. More money can be obtained from third-party sources for bugs in Apple software.
"People can get more cash if they sell their bugs to others," said Nikias Bassen, a security researcher for the company Zimperium, and who joined Apple's program last year. "If you're just doing it for the money, you're not going to give [bugs] to Apple directly."
Motherboard spoke to several members of Apple's bug bounty program with the condition of anonymity. Every single one said they had yet to report a bug to Apple and did not know anyone who had. iOS bugs are "too valuable to report to Apple," according to Patrick Wardle, a Synack researcher and former NSA hacker who was invited to the bug bounty program last year.
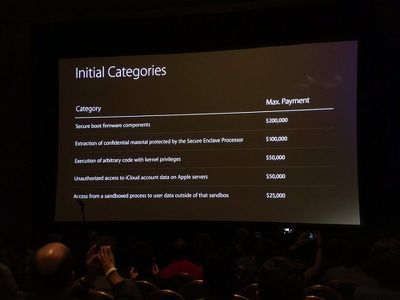
Apple first introduced its bug bounty program in August of 2016 at the Black Hat Conference, an annual global InfoSec event. Apple offers bounties of up to $200,000 depending on the vulnerability. Secure boot firmware components earn $200,000 at the high end, while smaller vulnerabilities, like access from a sandboxed process to user data outside of the sandbox, will earn $25,000.
Popular Stories
While the iPhone 17 Pro and iPhone 17 Pro Max are not expected to launch until September, there are already plenty of rumors about the devices.
Below, we recap key changes rumored for the iPhone 17 Pro models as of April 2025:
Aluminum frame: iPhone 17 Pro models are rumored to have an aluminum frame, whereas the iPhone 15 Pro and iPhone 16 Pro models have a titanium frame, and the iPhone ...
Apple may have updated several iPads and Macs late last year and early this year, but there are still multiple new devices that we're looking forward to seeing in 2025. Most will come in September or October, but there could be a few surprises before then.
We've rounded up a list of everything that we're still waiting to see from Apple in 2025.
iPhone 17, 17 Air, and 17 Pro - We get...
Apple's upcoming foldable iPhone (or "iPhone Fold") will feature two screens as part of its book-style design, and a Chinese leaker claims to know the resolutions for both of them.
According to the Weibo-based account Digital Chat Station, the inner display, which is approximately 7.76 inches, will use a 2,713 x 1,920 resolution and feature "under-screen camera technology." Meanwhile, the...
A common complaint about the iPad Pro is that the iPadOS software platform fails to fully take advantage of the device's powerful hardware.
That could soon change.
Bloomberg's Mark Gurman today said that iPadOS 19 will be "more like macOS."
Gurman said that iPadOS 19 will be "more like a Mac" in three ways:Improved productivity
Improved multitasking
Improved app window management...
Apple is preparing a "bold" new iPhone Pro model for the iPhone's 20th anniversary in 2027, according to Bloomberg's Mark Gurman. As part of what's being described as a "major shake-up," Apple is said to be developing a design that makes more extensive use of glass – and this could point directly to the display itself.
Here's the case for Apple releasing a truly all-screen iPhone with no...
Apple in October 2024 overhauled its 14-inch and 16-inch MacBook Pro models, adding M4, M4 Pro, and M4 Max chips, Thunderbolt 5 ports on higher-end models, display changes, and more. That's quite a lot of updates in one go, but if you think this means a further major refresh for the MacBook Pro is now several years away, think again.
Bloomberg's Mark Gurman has said he expects only a small...
Apple is working on a new version of the Vision Pro with two key advantages over the current model, according to Bloomberg's Mark Gurman.
Specifically, in his Power On newsletter today, Gurman said Apple is developing a new headset that is both lighter and less expensive than the current Vision Pro, which starts at $3,499 in the U.S. and weighs up to 1.5 pounds.
Gurman said Apple is also...
On this week's episode of The MacRumors Show, we catch up on the latest iOS 19 and watchOS 12 rumors, upcoming devices, and more.
Subscribe to The MacRumors Show YouTube channel for more videos
Detailed new renders from leaker Jon Prosser claim to provide the best look yet at the complete redesign rumored to arrive in iOS 19, showing more rounded elements, lighting effects, translucency, and...
It was a big week for leaks and rumors in the Apple world, with fresh claims about iOS 19, the iPhone 17 Pro, and even the 20th anniversary iPhone coming a couple of years from now.
Sources also spilled the tea on the inner turmoil at Apple around the Apple Intelligence-driven Siri revamp that has seen significant delays, so read on below for all the details on these stories and more!
iOS ...