LastPass has advised all users of the password manager to launch sites directly from the LastPass vault and enable two-factor authentication wherever possible, until it addresses a vulnerability discovered in LastPass browser extensions.
The client-side vulnerability, discovered by Google security researcher Tavis Ormandy, allows for an attack that is "unique and highly sophisticated", said LastPass in a blog post, without disclosing further details.
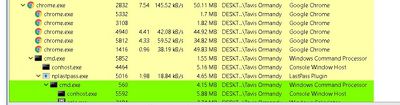
Ah-ha, I had an epiphany in the shower this morning and realized how to get codeexec in LastPass 4.1.43. Full report and exploit on the way. pic.twitter.com/vQn20D9VCy — Tavis Ormandy (@taviso) March 25, 2017
Over the weekend, Google security researcher Tavis Ormandy reported a new client-side vulnerability in the LastPass browser extension. We are now actively addressing the vulnerability. This attack is unique and highly sophisticated. We don’t want to disclose anything specific about the vulnerability or our fix that could reveal anything to less sophisticated but nefarious parties. So you can expect a more detailed post mortem once this work is complete.
To secure sign-in credentials in the meantime, LastPass has recommended that users launch sites directly from the vault and make use of two-factor authentication on sites that offer it, while remaining vigilant to avoid phishing attempts.
The news follows the discovery and successful patching of earlier remote code execution (RCE) vulnerabilities that could be used to steal passwords from extensions for Firefox, Chrome, Opera, and Edge. Safari was not mentioned in the original vulnerability alert, while mobile apps were not affected, but concerned users can follow the advice regardless until LastPass offers further news on the situation.



















Top Rated Comments
I only use iCloud for backups if I am having issues with my Mac which is the main place where I backup my devices.
I don't understand the hostility here?