Apple to Alert Users Who Installed Apps Compromised by XcodeGhost
 Apple has added an XcodeGhost question and answer page to its Chinese website today that explains what the malware is, how some users may be affected and next steps the company is taking to ensure that developers and end users alike are protected against malicious software going forward.
Apple has added an XcodeGhost question and answer page to its Chinese website today that explains what the malware is, how some users may be affected and next steps the company is taking to ensure that developers and end users alike are protected against malicious software going forward.
Apple claims that it has no evidence to suggest that XcodeGhost has been used for anything malicious, such as the transmission of personally identifiable information, stipulating that the code is only able to deliver some general information about apps and system information.
Nevertheless, Apple says it is working closely with developers and will soon list the top 25 most popular apps impacted by XcodeGhost on its Chinese website. The company will also be alerting users to let them know if they have downloaded apps that could have been compromised. Many affected apps have since been updated and are no longer infected by XcodeGhost.
Relevant portions of the Apple FAQ for users:
How does this affect me? How do I know if my device has been compromised?
We have no information to suggest that the malware has been used to do anything malicious or that this exploit would have delivered any personally identifiable information had it been used.
We’re not aware of personally identifiable customer data being impacted and the code also did not have the ability to request customer credentials to gain iCloud and other service passwords.
As soon as we recognized these apps were using potentially malicious code we took them down. Developers are quickly updating their apps for users.
Malicious code could only have been able to deliver some general information such as the apps and general system information.
Is it safe for me to download apps from App Store?
We have removed the apps from the App Store that we know have been created with this counterfeit software and are blocking submissions of new apps that contain this malware from entering the App Store.
We’re working closely with developers to get impacted apps back on the App Store as quickly as possible for customers to enjoy.
A list of the top 25 most popular apps impacted will be listed soon so users can easily verify if they have downloaded the latest versions of these apps. After the top 25 impacted apps, the number of impacted users drops significantly.
Customers will be receiving more information letting them know if they’ve downloaded an app/apps that could have been compromised. Once a developer updates their app, that will fix the issue on the user’s device once they apply that update.
We’re working to make it faster for developers in China to download Xcode betas. To verify that their version of Xcode has not been altered, they can take the following steps posted at
iPhone, iPad and iPod touch users should also read our XcodeGhost FAQ to learn more about the malware and how to keep yourself protected.
Apple also outlined steps for developers to validate Xcode using Terminal on OS X.
Popular Stories
While the iPhone 17 Pro and iPhone 17 Pro Max are not expected to launch until September, there are already plenty of rumors about the devices.
Below, we recap key changes rumored for the iPhone 17 Pro models as of March 2025:
Aluminum frame: iPhone 17 Pro models are rumored to have an aluminum frame, whereas the iPhone 15 Pro and iPhone 16 Pro models have a titanium frame, and the iPhone ...
Apple is expected to release iOS 18.4 to the general public as soon as next week, following more than a month of beta testing.
Apple's website says some iOS 18.4 features will be released in "early April," so the update should be out as early as Tuesday, April 1.
Apple this week seeded the iOS 18.4 Release Candidate, which is typically the final beta version, barring the discovery of any...
Leaker Jon Prosser today shared a mockup of what he says the Messages app will look like in iOS 19, demoing an interface with rounded, translucent bubble-shaped navigation buttons at the top and softer, rounder corners for the keyboard and word suggestions.
Jon Prosser's Messages app mockup
The return button, a button for going back to the Messages list, and the FaceTime button have a deeper...
If you pay for iCloud storage on your iPhone, Apple has a new perk for you, at no additional cost.
The new perk is the ability to create invitations in the Apple Invites app for the iPhone, which launched in the App Store last month.
In the Apple Invites app, iCloud+ subscribers can create invitations for any occasion, such as birthday parties, graduations, baby showers, and more. Anyone ...
Apple regularly refreshes the MacBook Pro models, and a new version that uses M5 series chips is in the works. Apple just finished refreshing most of the Mac lineup with M4 chips, and now it's time for the M5. Rumors suggest that we could see the first M5 MacBook Pro models this fall.
Design
There have been no rumors of a design update for the M5 MacBook Pro models that are coming this...
Apple today announced that AirPods Max with a USB-C port will be gaining support for lossless audio and ultra-low latency audio with a firmware update next month, alongside the release of iOS 18.4, iPadOS 18.4, and macOS 15.4.
For context, audio files are typically compressed to keep file sizes smaller. There are lossy compression standards like MP3 and AAC (Advanced Audio Codec), which...
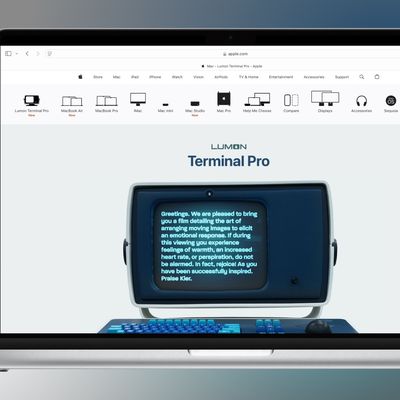
Apple is going all out with promotions for the popular Severance Apple TV+ show today, and as of right now, you'll find a new "Lumon Terminal Pro" listed on Apple's Mac site.
The Lumon Terminal Pro is designed to look similar to the machines that Severance employees like Mark S. and Helly R. use for macrodata refinement. The Terminal features a blue keyboard, a small display with wide...
The iOS 19 mockup images that leaker Jon Prosser shared today are not representative of the actual iOS 19 design, Bloomberg's Mark Gurman said on social media.
According to Gurman, the images that are "floating around" are based on "very old builds" or "vague descriptions," and are lacking key features. Gurman says that we can "expect more from Apple in June."
Gurman made the same comment ...
 Apple has added an XcodeGhost question and answer page to its Chinese website today that explains what the malware is, how some users may be affected and next steps the company is taking to ensure that developers and end users alike are protected against malicious software going forward.
Apple has added an XcodeGhost question and answer page to its Chinese website today that explains what the malware is, how some users may be affected and next steps the company is taking to ensure that developers and end users alike are protected against malicious software going forward.