Just days after Apple patched the DYLD_PRINT_TO_FILE security hole with the release of OS X 10.10.5, a developer has found a similar unpatched exploit that could allow attackers to gain root-level access to a Mac.
Luca Todesco shared information (via AppleInsider) on the "tpwn" exploit on GitHub over the weekend. It affects all versions of OS X Yosemite, including OS X 10.10.5, but does not affect OS X El Capitan.
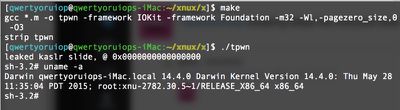
Todesco did not give Apple a heads up on the vulnerability before sharing it publicly, so it is not clear when Apple will release a patch for machines running OS X Yosemite. As noted by AppleInsider, it is standard procedure (and a courtesy) for security researchers and developers to provide Apple with details on vulnerabilities before publicizing them to prevent hackers from using security holes for nefarious purposes.
According to Todesco, who has also shared what he says is a third-party fix, releasing details on the exploit is no different than releasing an iOS jailbreak, but as Engadget explains, Todesco's actions have the potential to be somewhat more harmful than a jailbreak.
Those are technically true, but they downplay the practical dangers of publishing this info. Many people aren't knowledgeable enough to try third-party safeguards or deal with the possible side effects, and jailbreaks are at least intended for semi-innocuous purposes. A 'surprise' exploit for the Mac only really serves to give attackers time that they wouldn't otherwise have.
It took Apple less than a month to release OS X 10.10.5 to fix the DYLD_PRINT_TO_ACCESS vulnerability after it was first publicized, but during the time between its discovery and the launch of the fix, an exploit using the vulnerability was discovered in the wild.
Ahead of a fix for this latest vulnerability, OS X Yosemite users can protect themselves by downloading apps solely from the Mac App Store and from trusted developers.




















Top Rated Comments
Also, I think his comparison to jailbreaks is apt. Essentially whenever a jailbreak is released, the jailbreakers publish privilege escalation bugs and a nice demo on how to exploit them.
Finally, one should keep in mind that he could just as well have sold the exploit on the black market for a fat check instead of just publishing it and then getting called "complete jerk" as a reward ...
tl;dr: a lot of variables have to fall into place at the right time for this to have any major impact to a single machine.
BL.
Doesn't take away the fact that the guy was an idiot for releasing this the way he did.
Funnily enough, @i0n1c has a patch that can be applied to this.
BL.
* doesn't offer bug bounties
* sometimes doesn't even react to the bug reports
* when there's a reaction it uses to take months or more (and still some people praise them!?)
* doesn't always acknowledge the bug reporter
* doesn't EVEN make it easy to report and track bugs
So, again, what developer ethics are you talking about?