As noted by 9to5Mac, a Russian hacker has developed a relatively simple method to allow users to bypass Apple's In App Purchase mechanism on many iOS apps, allowing users to obtain the content for free.
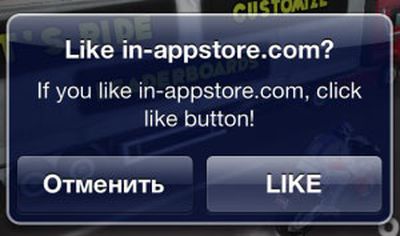
Alternate In App Purchase confirmation button seen on hacked devices
The method, which does not require jailbreaking, involves installing a pair of certificates on the user's device and then using a custom DNS entry. Users can then perform in-app purchases as usual and automatically be redirected through the hacked system.
Aside from the obvious impact that the hack involves theft of content from developers, the method also poses risks to those using the hack, as some of their own information is transmitted to the hacker's servers during the purchasing process. For both of those reasons, users are strongly advised not to pursue the method.
The hacker has already been evicted from his original host and had reportedly moved to a new one, but the site is currently down. It is unclear whether it is down simply due to high traffic or if other steps are being taken to hinder his activities.
Developers can prevent the hack from working with their apps by implementing validation of In App Purchase receipts, something many developers have not included in their apps.
Update: The Next Web takes a closer look at the method developed by Alexey Borodin, which actually can not be prevented simply by employing receipt validation.
All Borodin’s service needs is a single donated receipt, which it can then use to authenticate anyone’s purchase requests. Many of those receipts have been donated by Borodin himself, who has spent several hundred dollars on in-app purchases testing and generating receipts. [...]
Because the bypass emulates the receipt verification server on the App Store, the app treats it as an official communication, period.
Addressing the issue will ultimately require changes by Apple, which could enhance the API used for In App Purchases to provide for uniquely signed receipts that could not be duplicated on a mass basis as with Borodin's service.
The Next Web also interviewed Borodin, who noted that he has turned over operation of the site to a third party in order to avoid trouble and will be deleting any information he obtained from running the operation. According to Borodin, over 30,000 in-app transactions were made through his service, and he netted just $6.78 in PayPal donations to help with his costs.
Update 2: Macworld also chatted with Borodin, who noted that he can indeed see users' App Store account names and passwords, as they are transmitted in clear text as part of the In App Purchase process.
“I can see the Apple ID and password,” for accounts that try the hack, Borodin told Macworld. “But not the credit card information.” Borodin said that he was “shocked” that passwords were passed in plain text and not encrypted.
According to [developer Marco] Tabini, though, “Apple presumes it’s talking to its own server with a valid security certificate.” But that was clearly a mistake—“This is entirely Apple’s fault,” Tabini added.
Update 3: Apple has issued a brief statement to The Loop acknowledging that it is aware of and investigating the issue.
“The security of the App Store is incredibly important to us and the developer community, Natalie Harrison, told The Loop. “We take reports of fraudulent activity very seriously and we are investigating.”