Earlier this week, Gareth Wright disclosed his recent work showing that Facebook's app for iOS contains a security vulnerability that could allow malicious users to access login credentials held in a .plist file associated with the app. Obtaining a copy of that .plist file could allow a malicious users to automatically login in to the affected user's account on another device. The flaw reportedly also exists on Android devices.
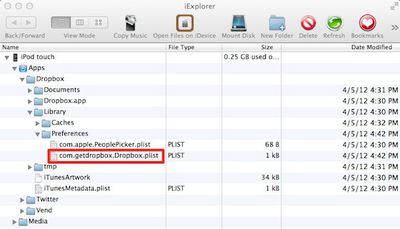
Wright first discovered the issue while using iExplorer to browse files on his iPhone, discovering that the Facebook .plist file maintains the full oAuth key and secret needed to access his account in plain text. Working with a friend, Wright was able to demonstrate that simply moving that .plist file to another device granted that device access to his Facebook account.
After backing up his own plist and logging out of Facebook he copied mine over to his device and opened the Facebook app…
My jaw dropped as over the next few minutes I watched posts appear on my wall, private messages sent, webpages liked and applications added.
Scoopz then opened Draw Something on his iPad which logged him straight into my account where he sent some pictures back to my friends.
Wright outlines a number of different ways in which a malicious user could obtain the login credentials, including customized apps, hidden applications installed on public PCs, or hardware solutions such as a modified speaker dock that could siphon the data.
Facebook has issued a statement claiming that the issue only affects devices that have been jailbroken or lost, as it requires either installation of a custom app or physical access to the device. But as pointed out by Wright and confirmed by The Next Web, unmodified devices need not be lost in order to be targeted, as simply plugging in a device to a compromised computer or accessory would be sufficient to allow the data to be gathered.
Furthermore, The Next Web has confirmed that the same issue affects Dropbox for iOS, similarly allowing a user to simply copy the .plist file from one device to another in order to gain access to the account. Given that two high-profile apps are vulnerable to credential theft, it seems likely that other services are also affected by the same issue.
As multiple reports note, there is no evidence that this method of collecting login credentials is actively being used in a malicious manner, and users can protect themselves for the time being by not connecting their devices to public computers or charging stations.
Update: While Wright's initial post claims that the issue affects "locked passcoded unmodified iOS Devices" when connected to a PC set up to capture the .plist file, The Next Web has now updated its report to indicate that in its testing the technique does not work on devices protected with a passcode.