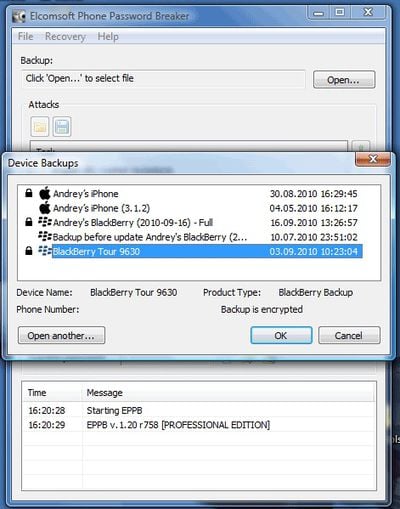
Bright Side of News reports that Russian forensics firm Elcomsoft has discovered a method of cracking Apple's hardware encryption built into iOS 4, providing law enforcement and other parties with a way to access the protected data provided they have physical access to the device.
According to Vladimir Katalov from Elcomsoft, you have to have physical access to the device that is being cracked into:
"Decryption is not possible without having access to the actual device because we need to obtain the encryption keys that are stored in (or computed by) the device and are not dumped or stored during typical physical acquisition."
Elcomsoft offers a basic Phone Password Breaker for Windows priced at $79 for home use and capable of unlocking encrupted backups of BlackBerry and iOS devices. A much more advanced package for iOS 4 devices is available for government agencies, offering access to other information such as passwords, stored email messages, and deleted SMS messages and emails.
Additional details on the decryption processes are available in a blog post on Elcomsoft's site.























Top Rated Comments
Even the non-simple passcode can be brute forced easily if the user doesn't follow basic secure password practices. Passwords should include at least one element from the upper case alphabet, lower case alphabet, numbers, and symbols while also being at least 8 characters long.
Using the escrow keys instead of brute forcing the passcode requires access to both the iOS device and a computer running iTunes with which that specific iOS device has been synced.
If you are really paranoid, just make sure that the passcode is sufficiently difficult to brute force and that you delete iTunes, making sure to remove any of it's associated files, after configuring (updating, etc) the iOS device.