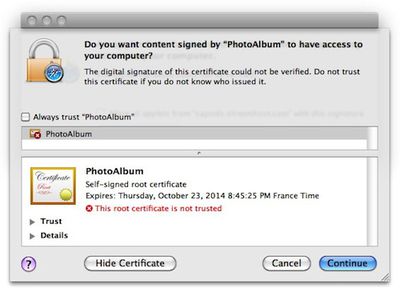
Security alert dialog box generated by malware's installation attempts
Yesterday, Mac antivirus firm SecureMac issued an alert regarding a new piece of malware capable of infecting systems running Mac OS X by using a trojan horse method of entry to deploy a Java-based payload enabling a wide variety of nefarious functions.
The trojan horse, trojan.osx.boonana.a, is spreading through social networking sites, including Facebook, disguised as a video. The trojan is currently appearing as a link in messages on social networking sites with the subject "Is this you in this video?"
When a user clicks the infected link, the trojan initially runs as a Java applet, which downloads other files to the computer, including an installer, which launches automatically. When run, the installer modifies system files to bypass the need for passwords, allowing outside access to all files on the system. Additionally, the trojan sets itself to run invisibly in the background at startup, and periodically checks in with command and control servers to report information on the infected system. While running, the trojan horse hijacks user accounts to spread itself further via spam messages. Users have reported the trojan is spreading through e-mail as well as social media sites.
Rival antivirus firm Intego responded with a notice of its own, downplaying the imminent threat from the malware due to the fact that it does not appear to be functioning as intended.
While Intego has evidence of several infections in the wild, we are not currently able to go beyond this step, as either the malicious malware has bugs preventing it from running correctly, or the servers it contacts are not active or are not serving the correct files.
Potentially, if it installs correctly, it functions the same as the Koobface worm running on Windows. It runs a local web server and an IRC server, acts as part of a botnet, acts as a DNS changer, and can activate a number of other functions, either through files initially installed or other files downloaded subsequently. It spreads by posting messages on Facebook, MySpace and Twitter, usually trying to get people to click a link to view some sort of video.
While this is an especially malicious piece of malware, the current Mac OS X implementation is flawed, and the threat is therefore low.
Both companies have conveniently noted that they offer products capable of identifying and eliminating the malware, although users without protection software should be alerted by the malware installation generating a Mac OS X dialog box regarding the attempted action.





















