Conversations in the Messages app feature end-to-end encryption that makes the content of the messages impossible to decipher, but according to documentation found by The Intercept, Apple tracks who its customers send iMessages to and is able to hand that information over to law enforcement when compelled to do so through a court order.
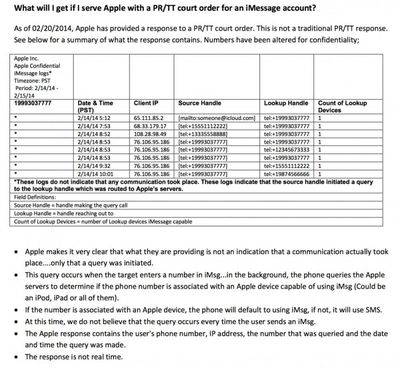
When a text message is sent to someone, the Messages app pings Apple's servers to see if the person has an iPhone or iPad in an effort to determine whether to send a message via iMessage or SMS. Each ping records date, time, number, and IP address, all of which is kept in a log that Apple says it stores for 30 days
Apple confirmed to The Intercept that it only retains these logs for a period of 30 days, though court orders of this kind can typically be extended in additional 30-day periods, meaning a series of monthlong log snapshots from Apple could be strung together by police to create a longer list of whose numbers someone has been entering.
The data on how Messages works was reportedly obtained by The Intercept from a document entitled "iMessage FAQ for Law Enforcement" that was given to the Florida Department of Law Enforcement's Electronic Surveillance Support Team. While labled "Law Enforcement Sources" and "For Official Use Only," it is not clear who wrote it.
As The Intercept points out, the documentation suggests that each number entered into the Messages app is transmitted to Apple when a new chat is opened, even if a conversation does not end up taking place. An Apple spokesperson said that the logging information in the iMessage FAQ is "generally accurate" but did not give additional data to make it clearer exactly when the Messages app pings Apple's servers. Apple did, however, give the following statement:
When law enforcement presents us with a valid subpoena or court order, we provide the requested information if it is in our possession. Because iMessage is encrypted end-to-end, we do not have access to the contents of those communications. In some cases, we are able to provide data from server logs that are generated from customers accessing certain apps on their devices. We work closely with law enforcement to help them understand what we can provide and make clear these query logs don't contain the contents of conversations or prove that any communication actually took place.
Apple takes a strong stance on privacy and promises to keep customer data private with tools like end-to-end encryption for the Messages app, but it has always maintained that there is some information that it is able to provide to law enforcement officials when compelled to do so.
Apple's website features a privacy section that details the information it collects and the types of data that it provides for government requests, including a full rundown of what's available to law enforcement [PDF]. Apple's documentation does not appear to mention Messages specifically, but it does specify that iCloud connection logs are retained for 30 days and that FaceTime calls logs are also maintained.
Note: Due to the political nature of the discussion regarding this topic, the discussion thread is located in our Politics, Religion, Social Issues forum. All forum members and site visitors are welcome to read and follow the thread, but posting is limited to forum members with at least 100 posts.