Israeli mobile software developer Cellebrite is helping the FBI in its attempt to unlock the iPhone at the center of the San Bernardino shooter investigation.
That's according to a story filed by Reuters this morning, based on a report in Wednesday's copy of Israeli daily newspaper Yedioth Ahronoth. If the software company succeeds then the FBI will no longer need the help of Apple, the report claimed, citing unnamed industry sources.
According to its website, Cellebrite offers "mobile forensics solutions" which "give access to and unlock the intelligence of mobile data sources to extend investigative capabilities, accelerate investigations, unify investigative teams and produce solid evidence".

Apple and the U.S. government have been embroiled in a heated public battle that started when a court ordered Apple to help the FBI unlock the iPhone 5c of terrorist Syed Farook. Unlocking the iPhone would require Apple to build a new version of iOS that bypasses iPhone passcode restrictions and provides the FBI with a way to enter passcodes electronically, something Apple has staunchly refused to do.
On Monday, the U.S. Justice Department convinced the court overseeing its ongoing battle with Apple to postpone a hearing scheduled to take place March 22. The DoJ said new leads had been discovered that could provide it with a way to unlock the iPhone 5c used by San Bernardino shooter Syed Farook without involving Apple.
Various commentators on the case have cast doubt on the FBI's original claim that it had exhausted all avenues in its attempt to unlock Farook's iPhone and a number of ideas have been floated in the media by security experts. The most likely attack was set out in a March 7 blog post by the American Civil Liberties Union (ACLU), which directly called into question the FBI's initial assertion that it had no means of extracting the iPhone's data.

The process described by UCLA technology fellow Daniel Kahn Gillmor uses a technique called NAND mirroring to copy the portion of the phone's memory that counts the number of passcode attempts entered. By continually restoring the copy, the FBI could thereby circumvent the limit on the number of passcode guesses that can be made before the device is rendered permanently inaccessible.
Another, more risky – not to mention laborious – method is an invasive microchip attack known as "de-capping". This involves removing and de-capsulating the phone's memory chip, carefully drilling down into it using a focused ion beam to expose the portion of the chip containing the target data (in this case, the iPhone's unique ID and passkey algorithm) and then probing it, micron by micron, to extract the information.
The latter could then be used in an off-device "brute-force" attack on the passcode that would be able to try all possible combinations without running up against the iPhone's guess limit.
The judge involved in the high-profile California case has agreed to vacate the March 22 hearing and requested that the government provide an update on its progress by April 5. The motion requiring Apple to help the FBI lock the iPhone was suspended.
In a conference call with reporters on Monday, Apple said it would insist on obtaining details about the exploit the FBI plans to use should the government keep the case going. If the case is dropped, Apple will not be able to ask for that information.
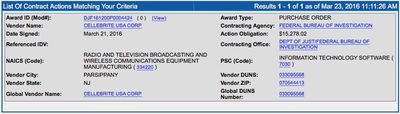
Update 8:13 AM: As noted by Twitter user @zenalbatross, the FBI signed a $15,000 contract with Cellebrite on Monday.
Note: Due to the political nature of the discussion regarding this topic, the discussion thread is located in our Politics, Religion, Social Issues forum. All forum members and site visitors are welcome to read and follow the thread, but posting is limited to forum members with at least 100 posts.