Older versions of Safari for Mac store unencrypted user login credentials in a plain text file, according to security firm Kaspersky (via ZDNet). Safari saves the information in order to restore a previous browsing session, reopening all sites, even those that require authentication using the browser's "Reopen All Windows from Last Session" functionality.
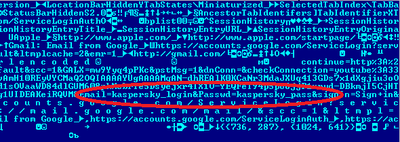
It turns out that Safari for Mac OS, like many other contemporary browsers, can restore the previous browsing session. In other words, all the sites that were open in the previous session – even those that required authorization – can be restored in a few simple steps when the browser is launched. Convenient? Of course. Safe? No, unfortunately.
Safari 6.0.5 for OS X 10.8.5 and 10.7.5 does not encrypt previous sessions, storing them instead in a standard LastSession.plist file that includes website usernames and passwords. Though the file is located in a hidden folder, it is still easily accessible and can be opened on any system.
Apple fixed this issue in Safari 6.1, which was released alongside OS X 10.9 Mavericks. Mac users running Mavericks or those who have installed the Safari 6.1 update for OS X 10.8 Mountain Lion or OS X 10.7 Lion will not be affected. This problem is limited to users running Safari 6.0.5 and can be remedied by upgrading to the latest software.





















Top Rated Comments
Storm in a teacup anyone?
But you need to enter the Master Password to see them and the file that contains the passwords on the filesystem has its contents encrypted so not the same at all
BOOM! You just sunk Kaspersky's battle ship.
If the password is visible in plaintext, it means the NSA will catch more terrorists. So this is basically a good thing.
</sarcasm off>