Flashback Malware's Ad-Click Hijacking Detailed, Could Reap $10,000/Day
Antivirus firm Symantec has published a new blog post examining how the Flashback malware affecting hundreds of thousand of Macs has been generating revenue for its authors by hijacking users' ad clicks. According to the report, the widespread nature of the infection means that malware authors could have been generating up to $10,000 per day from the scheme at its peak based on previous analysis of malware click redirection.
The Flashback ad-clicking component is loaded into Chrome, Firefox, and Safari where it can intercept all GET and POST requests from the browser. Flashback specifically targets search queries made on Google and, depending on the search query, may redirect users to another page of the attacker's choosing, where they receive revenue from the click . (Google never receives the intended ad click.)
Symantec's work on the ad-click hijacking aspect of Flashback comes after Russian firm Dr. Web, which was responsible for the initial publicity about the malware, published its own report examining some of the early data on infected computers seeking to connect to command-and-control servers.
The report looks at nearly 100,000 connections that came in on April 13, finding that close to two-thirds of the infected machines identified themselves as running Mac OS X Snow Leopard, which was the last version of OS X to ship with Java enabled by default. OS X Lion does not include Java by default, and thus was responsible for only 11% of infections seen during the survey period.
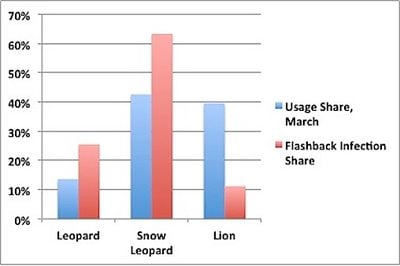 Flashback infection share vs. operating system usage share (Data via Dr. Web, Chart via Computerworld)
Flashback infection share vs. operating system usage share (Data via Dr. Web, Chart via Computerworld)As
noted by Computerworld, OS X Lion represents nearly 40% of OS X copies currently in use, suggesting that Apple's decision to remove Java from the default Lion install is indeed helping to limit infections on Apple's newest machines.
[W]hile Snow Leopard's and Leopard's infection rates are higher than their usage shares, the opposite's true of OS X 10.7, or Lion. The 2011 OS accounted for 39.6% of all copies of OS X used last month, yet represented only 11.2% of the Flashback-compromised Macs.
Dr. Web's data on OS kernel versions being reported from infected Macs also demonstrates that many Mac users do not keep their systems up-to-date, with roughly 25% of Snow Leopard and Lion systems seen in the survey reporting themselves as at least one version behind Apple's most recent updates (10.6.8 for Snow Leopard and 10.7.3 for Lion).
Popular Stories
While the iPhone 17 Pro and iPhone 17 Pro Max are not expected to launch until September, there are already plenty of rumors about the devices.
Below, we recap key changes rumored for the iPhone 17 Pro models as of March 2025:
Aluminum frame: iPhone 17 Pro models are rumored to have an aluminum frame, whereas the iPhone 15 Pro and iPhone 16 Pro models have a titanium frame, and the iPhone ...
Apple today released iOS 18.4 and iPadOS 18.4, the fourth major updates to the iOS 18 and iPadOS 18 operating system updates that came out last year. iOS 18.4 and iPadOS 18.4 come two months after Apple released iOS 18.3 and iPadOS 18.3.
Subscribe to the MacRumors YouTube channel for more videos.
The new software can be downloaded on eligible iPhones and iPads over-the-air by going to...
Apple's big developer event is a little over two months away, and rumors about what we can expect to see in Apple's next major operating system updates are becoming increasingly frequent.
A public release of iOS 18.4 is also imminent with a number of updates and improvements, although we won't be getting the major Apple Intelligence Siri upgrades that had reportedly been planned for this...
Apple is reportedly working on a new Magic Mouse. Below, we recap what to expect.
The two key rumors for the Magic Mouse 3 so far include a relocated charging port, along with a more ergonomic design.
It was briefly rumored that the Magic Mouse 3 would also feature voice control, but that was misinterpreted information.
Relocated Charging Port
While the Magic Mouse switched from...
With the second release candidate of iOS 18.4 that Apple seeded out today, the company finally provided us with release notes that give a full rundown on what to expect.
There's an Apple Vision Pro app, new Apple Intelligence features for notifications and additional language support, plus an Apple News Food feature for Apple News+ subscribers, and several updates that should improve the...
We've been hearing rumors about a foldable iPhone for almost a decade now, but it looks like we might finally see the device come to fruition in 2026. We're going to be waiting many more months for the foldable iPhone, but so far we're hearing good things.
Apple wants to make it creaseless. It's taken Apple multiple years to design a foldable iPhone that it's satisfied with because Apple ...
Multiple sources have claimed that iOS 19 will introduce a new design with more translucent buttons, menus, notification banners, and more, and there is now another clue that points towards this glass-like appearance.
Bloomberg's Mark Gurman today said the new design project is codenamed "Solarium" internally. A solarium is a room with glass walls that allow in plenty of sunlight, so this...
Apple today released macOS Sequoia 15.4, the fourth major update to the macOS Sequoia operating system that launched in September. macOS Sequoia 15.4 comes two months after the launch of macOS Sequoia 15.3.
Mac users can download the macOS Sequoia update through the Software Update section of System Settings. It is available for free on all Macs able to run macOS 15.
With...