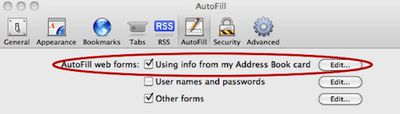
Earlier this week, The Register detailed a security vulnerability found in Apple's Safari Autofill feature that could enable malicious websites to extract users' personal information from their Address Book entries. The security researcher, Jeremiah Grossman of WhiteHat Security, followed up with a blog post yesterday detailing the exploit and offering a proof of concept webpage allowing users to see if they are vulnerable.
The vulnerability arises from Address Book's usage of simple form text fields to store the user's personal information, paired with Safari's ability to automatically grab that information through its Autofill feature to assist users with filling out web forms.
All a malicious website would have to do to surreptitiously extract Address Book card data from Safari is dynamically create form text fields with the aforementioned names, probably invisibly, and then simulate A-Z keystroke events using JavaScript. When data is populated, that is AutoFill'ed, it can be accessed and sent to the attacker.
For some reason, fields that begin with numbers such as phone numbers and street addresses are not subject to this vulnerability. A user's name, company affiliation, city/state/country, and email addresses can, however, typically be accessed.
Still, such attacks could be easily and cheaply distributed on a mass scale using an advertising network where likely no one would ever notice because it's not exploit code designed to deliver rootkit payload. In fact, there is no guarantee this has not already taken place. What is safe to say is that this vulnerability is so brain dead simple that I assumed someone else must have publicly reported it already, but exhaustive searches and asking several colleagues turned up nothing.
Grossman reports that he submitted information on the vulnerability to Apple on June 17th, but has received nothing more than an automatic acknowledgement of his submission despite an attempted follow-up. Consequently, Grossman is making public disclosure of the vulnerability so that users can take steps to protect themselves by disabling the Autofill feature, which is turned on by default.
Update: According to All Things Digital, Apple has acknowledged the issue and promised that it is working on a fix, but no timeframe for a release has been shared.